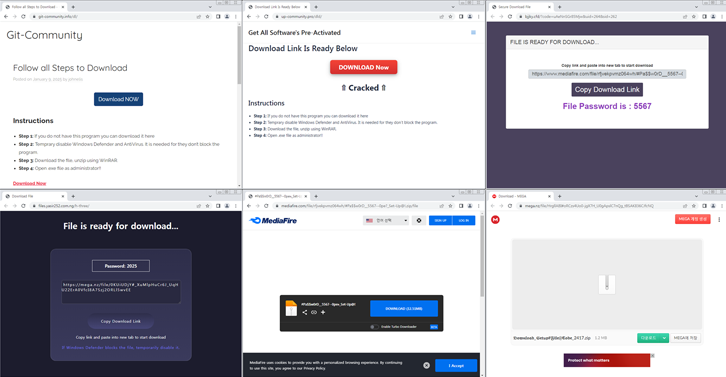
Cybersecurity experts are warning about a new malware campaign that uses cracked versions of software to distribute “Lumma” and “ACR Stealer.” AhnLab has noticed an increase in the distribution of ACR Stealer since January 2025, using a technique called “dead drop resolver” to extract the command-and-control (C2) server through legitimate services such as Steam, Google Forms, and Google Slides.
ACR Stealer can steal a wide range of information from compromised systems, including files, data from web browsers, and cryptocurrency wallets. Additionally, AhnLab has uncovered another campaign that uses files with the MSC extension, which are disguised as Word documents and executed through the Microsoft Management Console (MMC) to distribute a malware called Rhadamanthys.
Another risk comes from campaigns exploiting support platforms like Zendesk, where threat actors disguise themselves as customers to trick support agents into downloading Zhong Stealer. According to a report by Hudson Rock, over 30,000,000 computers have been infected by these malware, leading to the theft of corporate credentials and session cookies, which can be sold on hacker forums for personal gain.
Moreover, throughout the past year, malicious actors have increased efforts to distribute various malware, including stealers and remote access trojans (RATs), through a technique called ClickFix. This technique often involves redirecting users to fake CAPTCHA verification pages and executing malicious PowerShell commands.
Another payload that has been distributed is I2PRAT, which uses the I2P network to anonymize the command-and-control (C2) server, making it more difficult to track the threat. These developments highlight the significant danger that these malware campaigns pose to organizational security, offering malicious actors opportunities to exploit stolen credentials for personal profit.